When run, the backdoor copies itself to the Windows directory with the original name of the file it was run from or as SERVER.EXE, KERNEL16.DL, RUNDLL16.COM, SYSTEMTRAYICON!.EXE or WINDOW.EXE (names are different in different versions of SubSeven). Then it unpacks a single DLL file to the Windows System directory - WATCHING.DLL. This worm is also known as Backdoor.Subseven. Besides, backdoor-Sub7 : no update is required to detect and remove the server portion.
After that the backdoor patches Windows Registry so that its main application will be run during every Windows bootup (Run or RunServices keys). Finally, it creates and modifies some other Registry keys. The backdoor can also install itself to the system by modifying either the WIN.INI or the SYSTEM.INI file.
All the recent versions of SubSeven are supplied with a server configuration utility that allows it to customize server part capabilities - installation method, custom startup message, etc. This method was first introduced by the Back Orifice 2000 backdoor and it allows much more flexibility to backdoors.Below is a partial list of what Sub7 can do.
Below is a partial list of what Sub7 can do.
Monitor ALL of your online activity (purchases, chat, mail)
Open Web Browser to specified location
Restart Windows
Reverse Mouse buttons
Delete ANY of your files
Put ANY file on your computer
Record your passwords
Record your Keystrokes (on and off-line)
Open/Close your CD-ROM drive
Print Documents
Change screen resolution
Change Windows colors
Change Volume
Change Desktop wallpaper
Play sounds files
Play voice (using a Text to Speech engine)
Turn off the speakers
Change time/date
Update itself with a newer version
etc...
This trojan tends to escape virus detection due to the fact that it morphs, or changes a little each time its sent to a new victim.
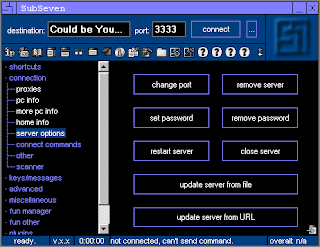
Main Window. Allows the hacker to change different server settings. As you can see, one of the options is completely removing the server from the host machine.
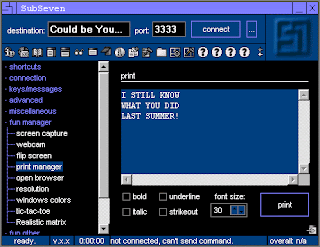
Print - Allows a hacker to print anything out on your home printer. This is typically used by the pranksters.
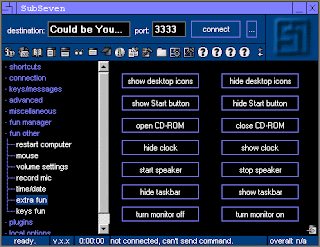
Fun Manager - One of the many "fun" features SubSeven offers. This is the prankster-toy side of this malware.
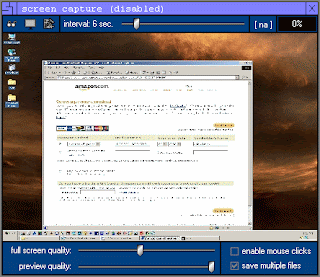
Screen Capture. Allows a hacker to receive continuous screen shots of your screen. This mean that whatever you see, chat, e-mail, online shopping, the hacker sees as well. These live feeds can actually be saved so the hacker can play it back like a movie and go over any information he/she might have missed.
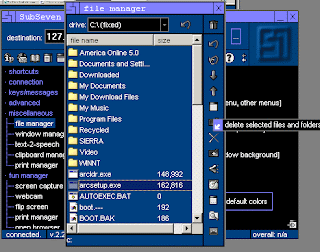
File Manager: Allows the hacker to copy, delete, rename, run any file on your computer.
How it loads, where it hides
It can be set to hide in just about any directory and can be loaded from the registry, system.ini, win.ini, and a few other less known places. Since the server editor that comes with Sub7 allows customization of startup, and the actual executable file, it is impossible to pinpoint the exact place Sub7 hides (since it's different with every file). What makes it even harder to find is that it can be assigned a different file name each time its ran, so every time you reboot your computer the file is somewhat altered (making it much harder to track down and delete).
Sub7 allows crackers to set a password on the server, theoretically so that once a machine is owned (infected), no other crackers can take control of it.The 2009 Subseven application tries to use ICQ, IRC and different e-mail accounts to notify the author that his victims are online.
All Sub7 components (files) should be deleted from an infected system for successful disinfection.
Open Web Browser to specified location
Restart Windows
Reverse Mouse buttons
Delete ANY of your files
Put ANY file on your computer
Record your passwords
Record your Keystrokes (on and off-line)
Open/Close your CD-ROM drive
Print Documents
Change screen resolution
Change Windows colors
Change Volume
Change Desktop wallpaper
Play sounds files
Play voice (using a Text to Speech engine)
Turn off the speakers
Change time/date
Update itself with a newer version
etc...
This trojan tends to escape virus detection due to the fact that it morphs, or changes a little each time its sent to a new victim.
Main Window. Allows the hacker to change different server settings. As you can see, one of the options is completely removing the server from the host machine.
Print - Allows a hacker to print anything out on your home printer. This is typically used by the pranksters.

Fun Manager - One of the many "fun" features SubSeven offers. This is the prankster-toy side of this malware.

Screen Capture. Allows a hacker to receive continuous screen shots of your screen. This mean that whatever you see, chat, e-mail, online shopping, the hacker sees as well. These live feeds can actually be saved so the hacker can play it back like a movie and go over any information he/she might have missed.

File Manager: Allows the hacker to copy, delete, rename, run any file on your computer.

How it loads, where it hides
It can be set to hide in just about any directory and can be loaded from the registry, system.ini, win.ini, and a few other less known places. Since the server editor that comes with Sub7 allows customization of startup, and the actual executable file, it is impossible to pinpoint the exact place Sub7 hides (since it's different with every file). What makes it even harder to find is that it can be assigned a different file name each time its ran, so every time you reboot your computer the file is somewhat altered (making it much harder to track down and delete).
Sub7 allows crackers to set a password on the server, theoretically so that once a machine is owned (infected), no other crackers can take control of it.The 2009 Subseven application tries to use ICQ, IRC and different e-mail accounts to notify the author that his victims are online.
All Sub7 components (files) should be deleted from an infected system for successful disinfection.


0 comments:
Post a Comment