The server part is installed on a remote system to be accessed. On execution of the PATCH.exe file the server part installs itself to Windows directory and it will be executed automatically during next Windows startup.
It can be an exe installer of itself, OR can be hidden inside a REAL setup.exe, usually planted in it and totally separate from whomever released the actual program. TROJ_NETBUS is the client component of the whole backdoor package and TROJ_SYSEDIT is the server component. The server component is used to infect a target computer and the client component is used to control a computer running the server component.
However, unlike other Backdoor Trojans, this backdoor package is not complete without the KEYHOOK.DLL file, (TROJ_NTBUS.54272) running in the infected system. The server part takes steps to protect itself from being removed from the system - it hides its process name in Windows task manager and denies access to file on attempt to delete or rename it.
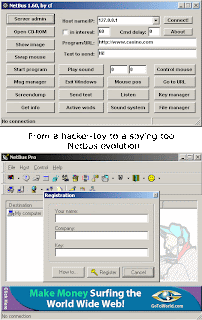
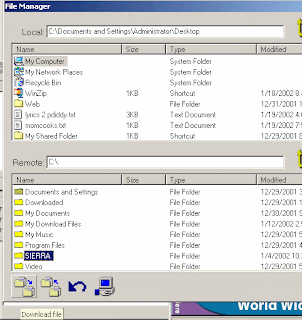
The client part allows to control the remote computer system where the server part is installed and activated. The client part has a dialog interface which allows to perform tricks (some of them are really nasty) on remote system and to receive/send data, text and other information.
 Back Orrifice pretty much offers the same features as NetBus. however it is a bit more flexible when it comes to editing the server program, and offers a slightly larger collection of destructive commands.
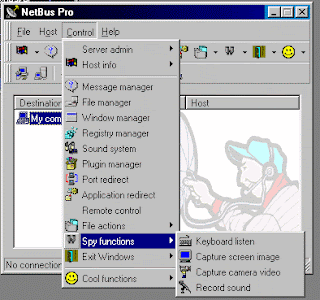
Back Orrifice pretty much offers the same features as NetBus. however it is a bit more flexible when it comes to editing the server program, and offers a slightly larger collection of destructive commands. Below is a partial list of what this trojan (Netbus) can do:
- Monitor ALL of your online activity (purchases, chat, mail)
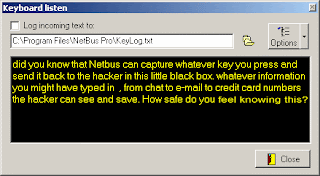
- Listen for keystrokes on remote system and save them to file
- Get a screenshot from remote computer
- Delete ANY of your files
- Put Return information about the target computer
- Record your Keystrokes (on and off-line)
- Open/Close your CD-ROM drive
- Print Documents
- Make click sounds every time a key is pressed
- Navigate you to unwanted and offensive web sites
- Edit your Registry
- Blocking certain keys on the remote system keyboard
- Redirect incoming connections
- Change Volume
- Change Desktop wallpaper
- Play sound files
- Turn off the speakers
- Password-protection management of the remote server
- Show, kill and focus windows on remote system
It will usually load up from the registry. Registry key commonly used by this malware:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices The previous versions of the server editor were much like server editor, they were meant to hide the server and perform destructive tasks.
Warning: To users whom have been scanned, either by our webpage scanner, or by our IRC bot, and were told they are infected. Please keep in mind, trojan loggers such as Jammer, AntiBO, and the like, are designed to trick potential hackers into thinking you are infected. This also has the same effect on our scanners.
If you are running such a program to log trojan connection attempts, then our scans may be seeing that, and not a trojan. For a true reading, please shut down the software and perform the scan again, then after getting true results, re-enable your trojan logger. You can remove this trojan manually from your computer. However, manual removal involves altering the Windows Registry.
.gif)
This program was designed as a remote admin tool, more so than as a hackers tool, however it is still possible to hide the server on a victims computer and use it for abuse. The main difference between 2.1 and 2.0 is features, not the way it tries to hide. However the removal is similar with only slight differences.
WARNING: Before making ANY changes to your systems registry, you should backup your registry (using the Export command in the registry menu), and Do Not edit or delete anything Other than what is recommended here. You can go to the Run command in your Start menu, and type regedit there to start the program.


0 comments:
Post a Comment