This guide will teach you how to flash/flex your Motorola ROKR E6 using RSD Lite. This guide assumes you have a firmware you'd like to flash.
Start your phone up in boot loader mode. To do this, hold down the camera button (top on the right side of the phone) and the Red power button at the same time. Your phone will boot up with a red screen which will say something similar to:FLASH_KEY_PRESS
Boot Module:
BOOT_G_00.02.21P_MACAU
MBM FLASH MODE
Now, connect your phone to your PC. You will see a Found New Hardware message with the Motorola Flash Interface, and perhaps a couple others.
Assuming you installed the drivers in the Get Connected section, you will then see the Your new hardware is installed and ready to use. message. If not, point Windows to your P2k drivers on the comp.
Open RSD Lite. I am using RSD Lite 3.5 in this tutorial, but I'm fairly sure anything 3.0 and up will work, maybe even previous versions. You should see a Model of NS Flash Bulverde and it should say Connected....
Click the ... button by the Filename menu and navigate to your firmware version you are installing. In this tutorial I am flashing R533_G_11.12.08P. Once you have the file selected (make sure its unrar'ed), click Start.
Your phone will now look like it is off. Its not, don't worry--there just isn't any screen which indicates your upgrading the software. Watch RSD Lite as it goes through its motions so you know where you're at in the process. The entire process of the flash took me about 10 minutes, give or take.
The phone will hang out at 99% for a long time--over a minute for mine. Don't worry, its fine. It will then reboot, and go through another few processes.
Assuming all went well, you will then see a PASS in RSD Lite.
Congrats! You have successfully flashed your Motorola ROKR E6!
Thursday, December 25, 2008
Flashing/Flexing your MOTO ROKR E6
Monday, December 22, 2008
INTRODUCTION to certifications
Cisco offers three levels of general IT certification namely associate, proffesional and expert(where CCIE represents the highest level of achievement). There are seven different tracks for you to choose so that you can match your certification path to your job role or industry. Apart from the general IT certs cisco also offers IT certs in Focused Areas through which network proffesionals can enhance their core networking knowledge by achieving specialist certification in technologies such as security,IP telephony, and wireless.
the seven tracks and their respective certs in the three levels are as per the table:
| General Certifications | |||
| Certification Paths | Associate | Professional | Expert |
Routing & Switching | CCNA | CCNP | CCIE Routing & Switching |
Design | CCNA & CCDA | CCDP | CCDE |
Network Security | CCNA Security | CCSP | CCIE Security |
Service Provider | CCNA | CCIP | CCIE Service Provider |
Storage Networking | CCNA | CCNP | CCIE Storage Networking |
Voice | CCNA Voice | CCVP | CCIE Voice |
Wireless | CCNA Wireless | Coming Soon! | CCIE Wireless |
back orifice
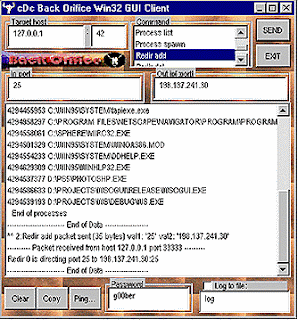
Back Orifice is a remote administration tool that allows system administrators to control a computer from a remote location (i.e. across the internet). It is a highly dangerous backdoor designed by a cracking group called the Cult of the Dead Cow Communications. It is usually distributed by malicious people in the form of aTrojan Horse attack During installation, it does not give any indication of what is really going on.To ease distribution, BO can also be attached to any other windows executable which will run normally after installing the server. Once installed, the server is intentionally difficult to detect on your machine.
The Back Orifice Server Contains the Following Functionality
System control
Create dialog boxes with the text of your choice. Log keystrokes. Lockup or reboot the machine.
Get detailed system information, including:
- current user
- cpu type
- windows version
- memory usage
- mounted disks
(including hard drives, cdroms, removable drives and remote network drives) and information for those drives - screensaver password
- passwords cached by the user
(including those for dialups, web and network access, and any other password cached by the operating system)
File system control
Copy, rename, delete, view, and search files and directories. File compression and decompression.
Copy, rename, delete, view, and search files and directories. File compression and decompression.
Application redirection
Spawn most console applications (such as command.com) on any TCP port, allowing control of applications via a telnet session.
Upload and download files on any port using a www client such as Netscape. Integrated packet sniffer Monitor network packets, logging any plaintext passwords that pass. Plugin interface Write your own plugins and execute the native code of your choice in BO's hidden system process. you can read more at http://www.irchelp.org/irchelp/security/bo.html http://boxp.sourceforge.net/smaug/smaug-index.php |
Thursday, December 18, 2008
SUB7(#1)
Sub7 or Subseven Gold (also known as Backdoor-G and all of its variants) is the most well known Trojan backdoor application availableThis trojan is the most popular and the most powerful Trojan Horse program available to the public.
When run, the backdoor copies itself to the Windows directory with the original name of the file it was run from or as SERVER.EXE, KERNEL16.DL, RUNDLL16.COM, SYSTEMTRAYICON!.EXE or WINDOW.EXE (names are different in different versions of SubSeven). Then it unpacks a single DLL file to the Windows System directory - WATCHING.DLL. This worm is also known as Backdoor.Subseven. Besides, backdoor-Sub7 : no update is required to detect and remove the server portion.
After that the backdoor patches Windows Registry so that its main application will be run during every Windows bootup (Run or RunServices keys). Finally, it creates and modifies some other Registry keys. The backdoor can also install itself to the system by modifying either the WIN.INI or the SYSTEM.INI file.
All the recent versions of SubSeven are supplied with a server configuration utility that allows it to customize server part capabilities - installation method, custom startup message, etc. This method was first introduced by the Back Orifice 2000 backdoor and it allows much more flexibility to backdoors.Below is a partial list of what Sub7 can do.
When run, the backdoor copies itself to the Windows directory with the original name of the file it was run from or as SERVER.EXE, KERNEL16.DL, RUNDLL16.COM, SYSTEMTRAYICON!.EXE or WINDOW.EXE (names are different in different versions of SubSeven). Then it unpacks a single DLL file to the Windows System directory - WATCHING.DLL. This worm is also known as Backdoor.Subseven. Besides, backdoor-Sub7 : no update is required to detect and remove the server portion.

After that the backdoor patches Windows Registry so that its main application will be run during every Windows bootup (Run or RunServices keys). Finally, it creates and modifies some other Registry keys. The backdoor can also install itself to the system by modifying either the WIN.INI or the SYSTEM.INI file.
All the recent versions of SubSeven are supplied with a server configuration utility that allows it to customize server part capabilities - installation method, custom startup message, etc. This method was first introduced by the Back Orifice 2000 backdoor and it allows much more flexibility to backdoors.Below is a partial list of what Sub7 can do.
Below is a partial list of what Sub7 can do.
Monitor ALL of your online activity (purchases, chat, mail)
Open Web Browser to specified location
Restart Windows
Reverse Mouse buttons
Delete ANY of your files
Put ANY file on your computer
Record your passwords
Record your Keystrokes (on and off-line)
Open/Close your CD-ROM drive
Print Documents
Change screen resolution
Change Windows colors
Change Volume
Change Desktop wallpaper
Play sounds files
Play voice (using a Text to Speech engine)
Turn off the speakers
Change time/date
Update itself with a newer version
etc...
This trojan tends to escape virus detection due to the fact that it morphs, or changes a little each time its sent to a new victim.
Main Window. Allows the hacker to change different server settings. As you can see, one of the options is completely removing the server from the host machine.
Print - Allows a hacker to print anything out on your home printer. This is typically used by the pranksters.
Fun Manager - One of the many "fun" features SubSeven offers. This is the prankster-toy side of this malware.
Screen Capture. Allows a hacker to receive continuous screen shots of your screen. This mean that whatever you see, chat, e-mail, online shopping, the hacker sees as well. These live feeds can actually be saved so the hacker can play it back like a movie and go over any information he/she might have missed.
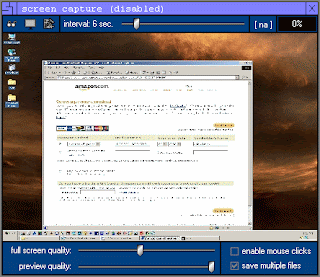
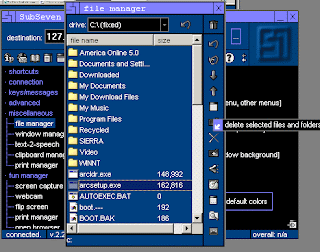
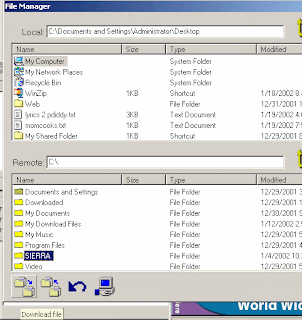
File Manager: Allows the hacker to copy, delete, rename, run any file on your computer.
How it loads, where it hides
It can be set to hide in just about any directory and can be loaded from the registry, system.ini, win.ini, and a few other less known places. Since the server editor that comes with Sub7 allows customization of startup, and the actual executable file, it is impossible to pinpoint the exact place Sub7 hides (since it's different with every file). What makes it even harder to find is that it can be assigned a different file name each time its ran, so every time you reboot your computer the file is somewhat altered (making it much harder to track down and delete).
Sub7 allows crackers to set a password on the server, theoretically so that once a machine is owned (infected), no other crackers can take control of it.The 2009 Subseven application tries to use ICQ, IRC and different e-mail accounts to notify the author that his victims are online.
All Sub7 components (files) should be deleted from an infected system for successful disinfection.
Open Web Browser to specified location
Restart Windows
Reverse Mouse buttons
Delete ANY of your files
Put ANY file on your computer
Record your passwords
Record your Keystrokes (on and off-line)
Open/Close your CD-ROM drive
Print Documents
Change screen resolution
Change Windows colors
Change Volume
Change Desktop wallpaper
Play sounds files
Play voice (using a Text to Speech engine)
Turn off the speakers
Change time/date
Update itself with a newer version
etc...
This trojan tends to escape virus detection due to the fact that it morphs, or changes a little each time its sent to a new victim.
Main Window. Allows the hacker to change different server settings. As you can see, one of the options is completely removing the server from the host machine.
Print - Allows a hacker to print anything out on your home printer. This is typically used by the pranksters.

Fun Manager - One of the many "fun" features SubSeven offers. This is the prankster-toy side of this malware.

Screen Capture. Allows a hacker to receive continuous screen shots of your screen. This mean that whatever you see, chat, e-mail, online shopping, the hacker sees as well. These live feeds can actually be saved so the hacker can play it back like a movie and go over any information he/she might have missed.

File Manager: Allows the hacker to copy, delete, rename, run any file on your computer.

How it loads, where it hides
It can be set to hide in just about any directory and can be loaded from the registry, system.ini, win.ini, and a few other less known places. Since the server editor that comes with Sub7 allows customization of startup, and the actual executable file, it is impossible to pinpoint the exact place Sub7 hides (since it's different with every file). What makes it even harder to find is that it can be assigned a different file name each time its ran, so every time you reboot your computer the file is somewhat altered (making it much harder to track down and delete).
Sub7 allows crackers to set a password on the server, theoretically so that once a machine is owned (infected), no other crackers can take control of it.The 2009 Subseven application tries to use ICQ, IRC and different e-mail accounts to notify the author that his victims are online.
All Sub7 components (files) should be deleted from an infected system for successful disinfection.
Wednesday, December 17, 2008
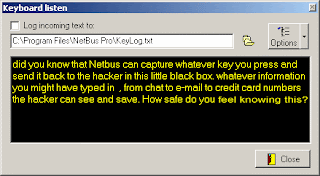
NETBUS(#2)
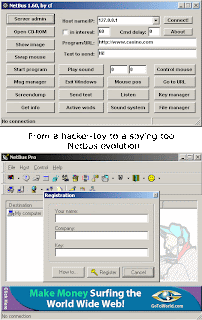
NetBus pro 2.0 is the second most popular Trojan Horse program available to the public (Sub7 is #1). Increased activity on TCP port 12345 -- best known as both the NetBus Trojan's default port.This is not a virus, but it is considered to be a trojan. It allows a hacker to access data and gain control over some Windows functions on remote computer system. This tool has client and server parts.
The server part is installed on a remote system to be accessed. On execution of the PATCH.exe file the server part installs itself to Windows directory and it will be executed automatically during next Windows startup.
It can be an exe installer of itself, OR can be hidden inside a REAL setup.exe, usually planted in it and totally separate from whomever released the actual program. TROJ_NETBUS is the client component of the whole backdoor package and TROJ_SYSEDIT is the server component. The server component is used to infect a target computer and the client component is used to control a computer running the server component.
However, unlike other Backdoor Trojans, this backdoor package is not complete without the KEYHOOK.DLL file, (TROJ_NTBUS.54272) running in the infected system. The server part takes steps to protect itself from being removed from the system - it hides its process name in Windows task manager and denies access to file on attempt to delete or rename it.
The client part allows to control the remote computer system where the server part is installed and activated. The client part has a dialog interface which allows to perform tricks (some of them are really nasty) on remote system and to receive/send data, text and other information.
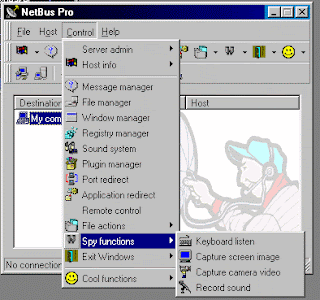 Back Orrifice pretty much offers the same features as NetBus. however it is a bit more flexible when it comes to editing the server program, and offers a slightly larger collection of destructive commands.
Back Orrifice pretty much offers the same features as NetBus. however it is a bit more flexible when it comes to editing the server program, and offers a slightly larger collection of destructive commands.
Below is a partial list of what this trojan (Netbus) can do:
![]() How it loads, where it hides:
How it loads, where it hides:
It will usually load up from the registry. Registry key commonly used by this malware:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices The previous versions of the server editor were much like server editor, they were meant to hide the server and perform destructive tasks.
Warning: To users whom have been scanned, either by our webpage scanner, or by our IRC bot, and were told they are infected. Please keep in mind, trojan loggers such as Jammer, AntiBO, and the like, are designed to trick potential hackers into thinking you are infected. This also has the same effect on our scanners.
If you are running such a program to log trojan connection attempts, then our scans may be seeing that, and not a trojan. For a true reading, please shut down the software and perform the scan again, then after getting true results, re-enable your trojan logger. You can remove this trojan manually from your computer. However, manual removal involves altering the Windows Registry.
.gif)
This program was designed as a remote admin tool, more so than as a hackers tool, however it is still possible to hide the server on a victims computer and use it for abuse. The main difference between 2.1 and 2.0 is features, not the way it tries to hide. However the removal is similar with only slight differences.
WARNING: Before making ANY changes to your systems registry, you should backup your registry (using the Export command in the registry menu), and Do Not edit or delete anything Other than what is recommended here. You can go to the Run command in your Start menu, and type regedit there to start the program.
The server part is installed on a remote system to be accessed. On execution of the PATCH.exe file the server part installs itself to Windows directory and it will be executed automatically during next Windows startup.
It can be an exe installer of itself, OR can be hidden inside a REAL setup.exe, usually planted in it and totally separate from whomever released the actual program. TROJ_NETBUS is the client component of the whole backdoor package and TROJ_SYSEDIT is the server component. The server component is used to infect a target computer and the client component is used to control a computer running the server component.

However, unlike other Backdoor Trojans, this backdoor package is not complete without the KEYHOOK.DLL file, (TROJ_NTBUS.54272) running in the infected system. The server part takes steps to protect itself from being removed from the system - it hides its process name in Windows task manager and denies access to file on attempt to delete or rename it.
The client part allows to control the remote computer system where the server part is installed and activated. The client part has a dialog interface which allows to perform tricks (some of them are really nasty) on remote system and to receive/send data, text and other information.
 Back Orrifice pretty much offers the same features as NetBus. however it is a bit more flexible when it comes to editing the server program, and offers a slightly larger collection of destructive commands.
Back Orrifice pretty much offers the same features as NetBus. however it is a bit more flexible when it comes to editing the server program, and offers a slightly larger collection of destructive commands. Below is a partial list of what this trojan (Netbus) can do:
- Monitor ALL of your online activity (purchases, chat, mail)
- Listen for keystrokes on remote system and save them to file
- Get a screenshot from remote computer
- Delete ANY of your files
- Put Return information about the target computer
- Record your Keystrokes (on and off-line)
- Open/Close your CD-ROM drive
- Print Documents
- Make click sounds every time a key is pressed
- Navigate you to unwanted and offensive web sites
- Edit your Registry
- Blocking certain keys on the remote system keyboard
- Redirect incoming connections
- Change Volume
- Change Desktop wallpaper
- Play sound files
- Turn off the speakers
- Password-protection management of the remote server
- Show, kill and focus windows on remote system
It will usually load up from the registry. Registry key commonly used by this malware:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices The previous versions of the server editor were much like server editor, they were meant to hide the server and perform destructive tasks.
Warning: To users whom have been scanned, either by our webpage scanner, or by our IRC bot, and were told they are infected. Please keep in mind, trojan loggers such as Jammer, AntiBO, and the like, are designed to trick potential hackers into thinking you are infected. This also has the same effect on our scanners.
If you are running such a program to log trojan connection attempts, then our scans may be seeing that, and not a trojan. For a true reading, please shut down the software and perform the scan again, then after getting true results, re-enable your trojan logger. You can remove this trojan manually from your computer. However, manual removal involves altering the Windows Registry.

.gif)
This program was designed as a remote admin tool, more so than as a hackers tool, however it is still possible to hide the server on a victims computer and use it for abuse. The main difference between 2.1 and 2.0 is features, not the way it tries to hide. However the removal is similar with only slight differences.
WARNING: Before making ANY changes to your systems registry, you should backup your registry (using the Export command in the registry menu), and Do Not edit or delete anything Other than what is recommended here. You can go to the Run command in your Start menu, and type regedit there to start the program.
Tuesday, December 16, 2008
ethical hacking seminar at TKR engineering college

today there was a seminar held at teegala krishna reddy engineering college on ethical hacking by the world renowned computer security and digital intelligence consultant ANKIT FADIA. he provided an insight into the need for information security necessary not only from the perspective of corporate worls but also from the perspective of an individual. he also provided a set of hacking demonstrations.
at the end of his session, he briefed the audience regarding the new,advanced Ankit Fadia Certified Ethical Hacker 3.0(a certification program on computer security). here are the details of the above mentioned program: it teaches you critical security skills and the latest tools and techniques being used in this field. the course duration is one month. AFCEH 3.0 is scheduled for the duration 9th Jan - 9th Feb.
Program highlights:
- 4 hrs of video conference with Ankit Fadia
- 12 hrs of self paced video on demand learning
- online discussion with other students and Ankit Fadia
- lab sessions and homework designed by Ankit Fadia
- selected participants get chance to meet Ankit Fadia in person
the program is suitable for both experinced computer security specialists as well as for beginners .
Registration:
You need to register for AFCEH 3.0 as there are limited seats. you can register yourself at your nearest Reliance World or you can log on to http://www.hackingmobilephones.com/afceh/
for further queries you can log on to the same site http://www.hackingmobilephones.com/afceh/or http://www.relianceworld.in/afceh-upgrade.htm
Monday, December 15, 2008
recognize scam e-mails
*Phishing - Defined as the practice of luring unsuspecting people to a fake website by using authentic-looking e-mail, sometimes even using the real organization's logo, in an attempt to steal your valuable personal data, such as credit card numbers, passwords, account data, or other information.
MICROSOFT's e-mail to help all Hotmail users recognise the scam e-mails that do sneak by our filters. these are the top 5 ways to protect yourself from phishing and scam e-mails.
1) Be wary of e-mails asking for your personal information.
Any e-mail asking for your name, birth date, e-mail username, e-mail password, or any other type of personal information, no matter who the e-mail appears to be from, is almost certainly a scam.
If you have any reason to believe it may be legitimate, do not reply to the e-mail or click any hyperlinks; instead copy and paste the web URL or go to that company's website for contact information. Don't hesitate to contact the company's support channel to confirm legitimacy.
2) Carefully read e-mails that appear suspicious.
E-mails that are poorly worded, have typos, or have phrases such as "this is not a joke" or "forward this message to your friends" are generally scam e-mails. Sometimes company names or brands are misspelled or inaccurate; such as saying Windows Hotmail (instead of Windows Live™ Hotmail).
3) Protect your Hotmail password.
Create a strong password for your Hotmail account by using more than 7 characters and having a combination of upper and lower case characters, numbers, and special characters, like the @ or # symbols. It's also a good idea to change your password on a regular basis. Learn More.
If you receive a notification from Microsoft Customer Support confirming your request to change your password, as I did this past week, and you haven't recently changed your password, that's a signal that someone else may be trying to gain access to your Hotmail account, and you should immediately change your password. To do so, either go to http://account.live.com/, or within Hotmail, click Options, then View and Edit your Personal Information. You will be prompted to log in again. Once you do, look for "Password reset information" under your name at the top. Change both your password and your Secret Question/Secret Answer as both may have been compromised.
4) Take action!
If you think someone has accessed your Hotmail account, that the Windows Live ID sign-in page looks fraudulent, or you receive a suspicious e-mail that tries to confirm a password change you didn't authorise, change your password immediately via the instructions above, or go to: http://account.live.com/.
5) the users can contribute from their side to help MICROSOFT identify new scams.
If you're using the Full version of Hotmail, you can select the dropdown next to "Junk", then select "Report phishing scam". Whatever you do, do not reply back to the sender.
MICROSOFT's e-mail to help all Hotmail users recognise the scam e-mails that do sneak by our filters. these are the top 5 ways to protect yourself from phishing and scam e-mails.
1) Be wary of e-mails asking for your personal information.
Any e-mail asking for your name, birth date, e-mail username, e-mail password, or any other type of personal information, no matter who the e-mail appears to be from, is almost certainly a scam.
If you have any reason to believe it may be legitimate, do not reply to the e-mail or click any hyperlinks; instead copy and paste the web URL or go to that company's website for contact information. Don't hesitate to contact the company's support channel to confirm legitimacy.
2) Carefully read e-mails that appear suspicious.
E-mails that are poorly worded, have typos, or have phrases such as "this is not a joke" or "forward this message to your friends" are generally scam e-mails. Sometimes company names or brands are misspelled or inaccurate; such as saying Windows Hotmail (instead of Windows Live™ Hotmail).
3) Protect your Hotmail password.
Create a strong password for your Hotmail account by using more than 7 characters and having a combination of upper and lower case characters, numbers, and special characters, like the @ or # symbols. It's also a good idea to change your password on a regular basis. Learn More.
If you receive a notification from Microsoft Customer Support confirming your request to change your password, as I did this past week, and you haven't recently changed your password, that's a signal that someone else may be trying to gain access to your Hotmail account, and you should immediately change your password. To do so, either go to http://account.live.com/, or within Hotmail, click Options, then View and Edit your Personal Information. You will be prompted to log in again. Once you do, look for "Password reset information" under your name at the top. Change both your password and your Secret Question/Secret Answer as both may have been compromised.
4) Take action!
If you think someone has accessed your Hotmail account, that the Windows Live ID sign-in page looks fraudulent, or you receive a suspicious e-mail that tries to confirm a password change you didn't authorise, change your password immediately via the instructions above, or go to: http://account.live.com/.
5) the users can contribute from their side to help MICROSOFT identify new scams.
If you're using the Full version of Hotmail, you can select the dropdown next to "Junk", then select "Report phishing scam". Whatever you do, do not reply back to the sender.
Wednesday, December 10, 2008
MICROSOFT WINDOWS SERVER

Windows Server is a brand name for server operating systems released by Microsoft Corporation. the version history of windows networking operating systems goes this way:
Windows NT 3.1 (1983)
Windows NT 3.5 (1994)
Windows NT 4.0 (1996)
Windows NT 5.0/ MS Windows 2000
Windows NT 5.2/ MS Windows 2003
Windows Server 2008 (2008)
this subject would be much more ideal for presentation than other as this product comes in with wide range of features.some of the features of the windows 2003 are as follows:
- built on NT technology
- availability
- scalability
- easy installation
- larger h/w support(supports plug n play)
- in-built terminal services
- active directory
- secondary log on services
- remote installation service
- improved security-(kerberos 5, internet proto security,smart card)
- distributed file system
- centralized deployment of applications
- DNS dependency
- backup on any media
- supports FAT16, FAT32,NTFS
- volume shadow copy
- disk quotas
though the features are self explanatory by their name, if any of you have a query in any of those u can post in ur comment i ll get back to you as soon as possible. now, as we have the latest windows server version released lets just check some of the basic differences:
MS Windows server 2003 vs MS Windows server 2008
- no read only Domain controller == read only domain controller
- no in-built group policy mgmt console == in-built gpmc
- no windows server core == windows server core
- IIS 6.0 == IIS 7.0
- no network discovery service == network discovery service
- 4 primary partitions == 3 primary partitions
- no shrinking volumes == shrinking volumes
- remote installation service == (name changed)windows deployment services
Saturday, December 6, 2008
session 1: MICROSOFT VISUAL STUDIO
Microsoft visual studio is an integrated devleopment environment(IDE) developed by microsoft. It can be used to develop console/graphical interface applications, websites, web services and other web applications. Apart from supporting all the platforms of Microsoft Windows,Windows Mobile, Windows CE, .NET Framework, .NET Compact Framework and Microsoft Silverlight, it admits a code editor that supports Intellisense(implementation of autocompletion) and code refactoring(enables code alteration of a program inorder to simplify its structure,improve its readibility while preserving its functionality).The integrated debugger provided can be utilized as a source-level debugger and a machine-level debugger. Built-in languages include C/C++ (via Visual C++), VB.NET (via Visual Basic .NET), and C# (via Visual C#). Support for other languages such as Chrome, F#, Python, and Ruby among others has been made available via language services which are to be installed separately. It also supports XML/XSLT, HTML/XHTML, JavaScript and CSS.
version history
1. visual studio 97 ----> 1997
2. visual studio 6.0----> 1998
3. visual studio .NET(2002)----> 2002
4. visual studio .NET(2003)----> 2003
5. visual studio 2005
6. visual studio 2008
7. visual studio 2010 (being developed)
version history
1. visual studio 97 ----> 1997
2. visual studio 6.0----> 1998
3. visual studio .NET(2002)----> 2002
4. visual studio .NET(2003)----> 2003
5. visual studio 2005
6. visual studio 2008
7. visual studio 2010 (being developed)
session2: MICROSOFT SQL SERVER
Microsoft SQL Server is a relational database management system (RDBMS) produced by Microsoft. Its primary query languages are MS-SQL and T-SQL. MS-SQL is nothing but Microsoft's database computer language designed for the retrieval and management of data in RDBMS, database schema creation and modification, and database object access control management and T-SQL is Microsoft's and Sybase's proprietary extension to SQL.When it comes to performance, MS SQL’s strength of being packed with more features than other systems is its biggest disadvantage. it comes with adequate security mechanisms by default, bearing you follow the directions and keep the software updated with security patches.The good thing about MS SQL is that it allows you to change ports in case the default becomes too vulnerable. another advantage with MS-SQL server is that the data corruption is more unlikely. The data travels through various checkpoints while passing from your keyboard to the hard disk and through the monitor. apart from that the MS-SQL Server keeps track of the process, even if the system unexpectedly shuts down.
history:
-1987 Sybase releases SQL Server for UNIX.
- 1988 Microsoft, Sybase, and Aston-Tate port SQL Server to OS/2.
- 1989 Microsoft, Sybase, and Aston-Tate release SQL Server 1.0 for OS/2.
- 1990 SQL Server 1.1 is released with support for Windows 3.0 clients.
(Aston-Tate drops out of SQL Server development)
- 1992 Microsoft SQL Server 4.2 for 16-bit OS/2 1.3 is released.
- 1992 Microsoft and Sybase port SQL Server to Windows NT.
- 1993 Microsoft and Sybase release version 4.2 of SQL Server for Windows NT.
(Microsoft and Sybase co-development of SQL Server officially ends.Microsoft continues to develop the Windows version of SQL Server.Sybase continues to develop the UNIX version of SQL Server)
- 1995 Microsoft releases version 6.0 of SQL Server.
- 1996 Microsoft releases version 6.5 of SQL Server.
- 1998 Microsoft releases version 7.0 of SQL Server.
- 2000 Microsoft releases SQL Server 2000.
- 2001 Microsoft releases XML for SQL Server Web Release 1.
- 2002 Microsoft releases SQLXML 2.0 (renamed from XML for SQL Server).
- 2002 Microsoft releases SQLXML 3.0.
- 2005 Microsoft releases SQL Server 2005
- 2008 Microsoft releases SQL Server 2008
history:
-1987 Sybase releases SQL Server for UNIX.
- 1988 Microsoft, Sybase, and Aston-Tate port SQL Server to OS/2.
- 1989 Microsoft, Sybase, and Aston-Tate release SQL Server 1.0 for OS/2.
- 1990 SQL Server 1.1 is released with support for Windows 3.0 clients.
(Aston-Tate drops out of SQL Server development)
- 1992 Microsoft SQL Server 4.2 for 16-bit OS/2 1.3 is released.
- 1992 Microsoft and Sybase port SQL Server to Windows NT.
- 1993 Microsoft and Sybase release version 4.2 of SQL Server for Windows NT.
(Microsoft and Sybase co-development of SQL Server officially ends.Microsoft continues to develop the Windows version of SQL Server.Sybase continues to develop the UNIX version of SQL Server)
- 1995 Microsoft releases version 6.0 of SQL Server.
- 1996 Microsoft releases version 6.5 of SQL Server.
- 1998 Microsoft releases version 7.0 of SQL Server.
- 2000 Microsoft releases SQL Server 2000.
- 2001 Microsoft releases XML for SQL Server Web Release 1.
- 2002 Microsoft releases SQLXML 2.0 (renamed from XML for SQL Server).
- 2002 Microsoft releases SQLXML 3.0.
- 2005 Microsoft releases SQL Server 2005
- 2008 Microsoft releases SQL Server 2008
Microsoft Student Partner:rythmic sessions
the MSP tag surely adds a lot to your resume but there a couple of activities that have to be performed as a part of the student partnet program. one such activity is the ryhtmic sessions. as the name suggests, the MSPs need to deliver sessions on a set of subjects. with an intention to aid other newly recruited MSPs i am publishing posts with brief overview on each of the topic on which a session can be delivered. i hope these posts provide a basic idea and hence help the MSPs in some or the other way.
Wednesday, December 3, 2008
they(police n armed forces) "DIED" so that mumbai cud "LIVE"
the title i have given was quoted by one of the english news channels,i prefered to give this title because this really hit me hard and deep and it really speaks a lot and so i would like to begin this post by SALUTING THE MARTYRS(probably they deserve a lot more). i hope the politicians realize their duty atleast now instead of just finding scapegoats and play the blame game, they need to understand they are not leaders but they are PUBLIC SERVANTS. there were many terror attacks earlier as well but it wasn't as audacious as this one. people just showed their patriotism for a week or at the most a month and then were back to normal life, which actually gave the politcians a great way to escape. this time its not the case people felt the pinch, the attack had a huge impact on the youth and other age groups and probably hence they have come to the conclusion "enough is enough".it is now that the citizens of our country have realized that there was something more that they need to contribute, apart form just trying to earn money for themselves, to make our country prosper and secure. the politicians shud not take the people for granted anymore and stop using terror attacks as a means to their vote banks.there is a lot of mess to be cleared by the politcians in which the none other than we the people of INDIA play an important role.here i wud like to present some of the views that i feel wud really contribute to INDIA's better tomorrow:
- there are many things at this moment that we need to re-build apart from just the damage incurred at the TAJ and the OBEROI-TRIDENT ,these things are nothing but the security council reforms.
- telecast the necessary meetings of the government and the politicals parties that may provide better view to the citizens of the country in identifying politicians providing good measures and also those that oppose those good measures.this way the people wud vote intelligently on the basis of the politician's ideas and views.
- this has been one of the major concerns. people who work all day n never sleep so that we can sleep pleasantly are not paid well. their job and the salary they receive are not justified.the government should not hesistate on imposing a rule that states that all the employees of the govt. companies and MNCs must contribute a certain amount from their monthly salary and it must be used only and only for paying the armed forces people of our country a little more.
- every year the government must select certain IIM/IIT students to be a part of their meetings and take their assistance in planning not only the economical aspect but also the security aspect of the country by providing the essential technology assistance and proper utilization of capital for the armed forces.
- last thing that i want to mention is that there must be a 1 hour show telecasted on all news channels on weekends that totally focuses and create awareness on people's rights as the citizen of our country
Subscribe to:
Comments (Atom)
